Explain Different Types of Security Threats in E Commerce
Hence it is an important factor for all business applications to handle the real-time traffic and overcome other performance problems for which performance testing should be taken up with testing services. Whether your application is an E-commerce website or a mobile app or any other system it should be well tested to show effective performance characteristics.
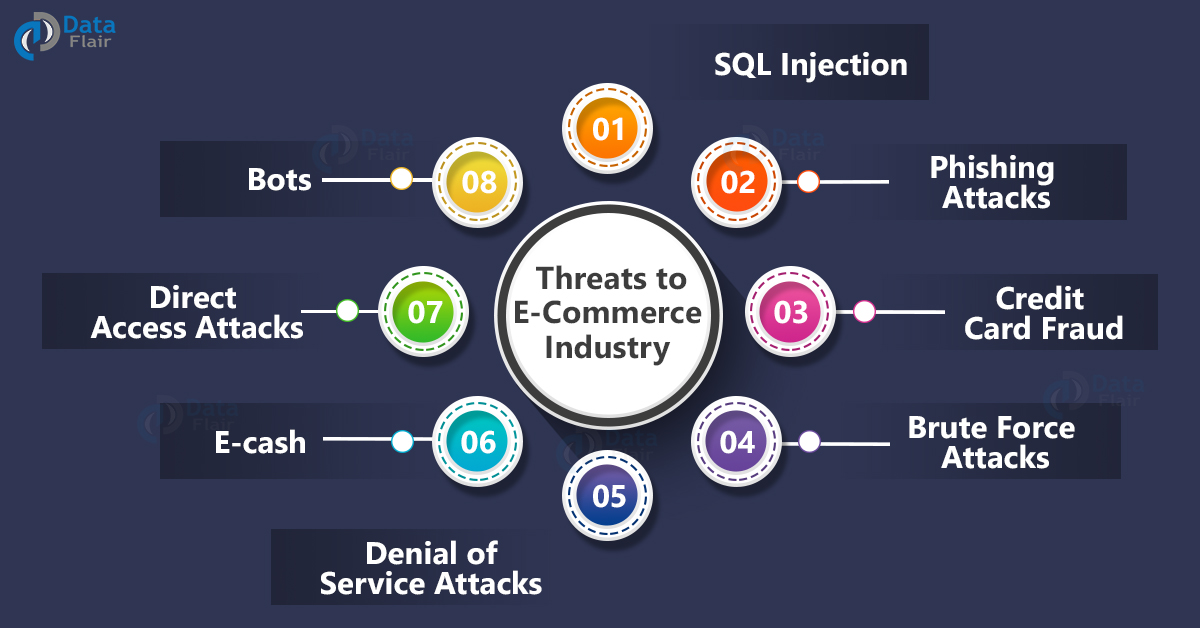
E Commerce Security Threats And Their Solutions Dataflair
In the paragraphs that follow I explain the various numeric data types available in RPG IV.

. Key USPs- The course is created in a well-structured order Concepts are clearly. You should not manage or treat in the same way all types of risk. From their experience they are able to work on the most difficult assignments.
Strategic risk - eg a competitor coming on to the market. Then I explain the binary number types. You should understand what type of risk you are facing before you consider how to deal with it.
We are also able to handle any complex paper in any course as we have employed professional writers who are specialized in different fields of study. But the Internet security protocol helps in the security and integrity of data over the internet. The following are some of the course we offer assignment help in.
Financial risk - eg interest rate. First I explain the decimal types because they are the ones most used in databases. In this work we are exploring the background of IoT systems and security measures and identifying a different security and privacy issues b approaches used to secure the components of IoT.
There are different types of protocol exist like routing mail transfer and remote communication protocol. These include Usable Security Software Security Cryptography and Hardware Security. The main four types of risk are.
Compliance and regulatory risk - eg introduction of new rules or legislation. It starts with the fundamental concepts required for building a secure system. All the different aspects and types of security are covered over the 5 sections.
This is followed by a final project. Naturally two way communication is achieved by having a single device being capable of both modulation and demodulation from which the unit takes its name. If you are new to the AS400 but have programmed in languages like C Pascal or BASIC you have used the binary types but you may not be familiar.
In todays world we transfer the data in bulk and the security of this data is very important so Internet security provides that feature ie protection of data. Different frequencies can then represent different groups of binary digits in a process which is known as modulation when it is being transmitted and demodulation when it is decoded at the receiving end. Types of business risks.
We offer assignment help in more than 80 courses.

Top E Commerce Security Threats And Solutions In 2020 Temok Hosting Blog

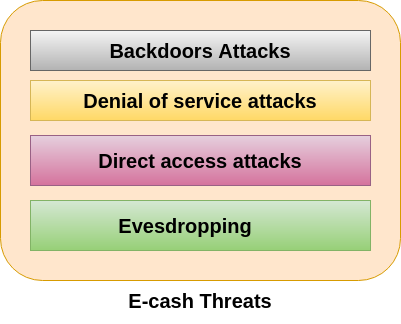
Comments
Post a Comment